The cyber threat landscape is constantly evolving, and cyber-resilient SMEs need to be proactive. Cyber-attacks are becoming more sophisticated, and businesses must protect themselves against them. There are some tried and true ideas, such as the 3-2-1 backups, but becoming genuinely cyber resilient requires a strategic and holistic approach.
To help you sort through the complexity, in this blog post, we’ll take a deep dive into how SMEs can be cyber-resilient in 2022.
A crash course on cyber-resilience
We explored the topic of “What is Cyber-Resilience?” in a previous article, so I’ll give you the short version here. We define cyber-resilience as “an organization’s ability to recover from an adverse cyber-event”. In simple terms, that means cyber-resilience is about how well you can bounce back if something goes wrong.
For modern SMEs, “something” in this case can be a ransomware attack, a malicious user, account deletion, a natural disaster, or any number of other threats. Lack of cyber-resilience can lead to anything from being forced out of business to paying ransoms to hackers.
That’s the “what” of cyber-resilience, but the “how” is really where it gets interesting.
Often, when people think of cyber-resilience, they think it’s all about backup and recovery. While backup and recovery are important, true cyber-resilience requires a comprehensive approach that includes robust infrastructure security, cyber threat assessments, documented security policies, risk detection and management tools, and compliance audits.
To better understand the “how” of cyber-resilience, let’s take a useful model SMEs can use to develop a robust strategy.
A cyber-resilience framework for SMEs
There have been a variety of approaches to thinking about cyber-resilience over the last decade. For example, NIST SP 800-160 Developing Cyber-Resilient Systems: A Systems Security Engineering Approach takes a rigorous approach to cyber-resilience. Similarly, the Cybersecurity and Infrastructure Security Agency (CISA) publishes Cyber Resilience Review (CRR) resources to help organizations assess and improve their cyber-resilience.
However, from the perspective of the modern SME looking for a place to start, the five components of cyber-resilience outlined in Symantec’s The Cyber Resilience Blueprint: A New Perspective on Security whitepaper provide us with the most pragmatic framework. The five components (prepare/identify, protect, detect, respond, and recover) are robust enough to account for all the high-level considerations a SME must consider without being prohibitively complex.
Let’s look at each and how they can help you develop a plan for cyber-resilience.
- Prepare / Identify – The first step is to conduct an infrastructure assessment and ask questions like: “what are my most important assets?”, “where is my data located?”, “what security controls are already in place today?” etc. These will help to determine the different systems and data that need protecting, and identify how much risk your business is willing to take for each.
- Protect – Here you take action to protect your assets and data, according to the risk profiles identified in the first step. Security appliances, endpoint protection, hardening operating systems and applications, and user education are all vital in this stage. Many breaches result from user error, and SMEs must protect against this attack vector.
- Detect – Detection is all about rapidly detecting threats in real-time. Technology like anti-malware engines, intrusion detection systems, and network monitoring platforms that alert IT to threats, are standard tools that can help. Early detection is key to limiting the follow on events of a breach, so investment here can pay dividends.
- Respond – Once you detect a threat, how fast can you respond to it and how effective is that response? There are security solutions that can automate this, but there will always be a human element to incident response. Notifications that get the right people aware of an issue quickly, and training so they know what to do, can support effective response.
- Recover – SMEs must have contingencies to account for disasters. Even with the best security tooling and planning, failure to have a reliable backup and recovery strategy can be a fatal flaw in a SME’s security posture. Because recovery is so important to a cyber-resilience strategy, we’ve created the 4 pillars of cyber-recovery to help you get it right.
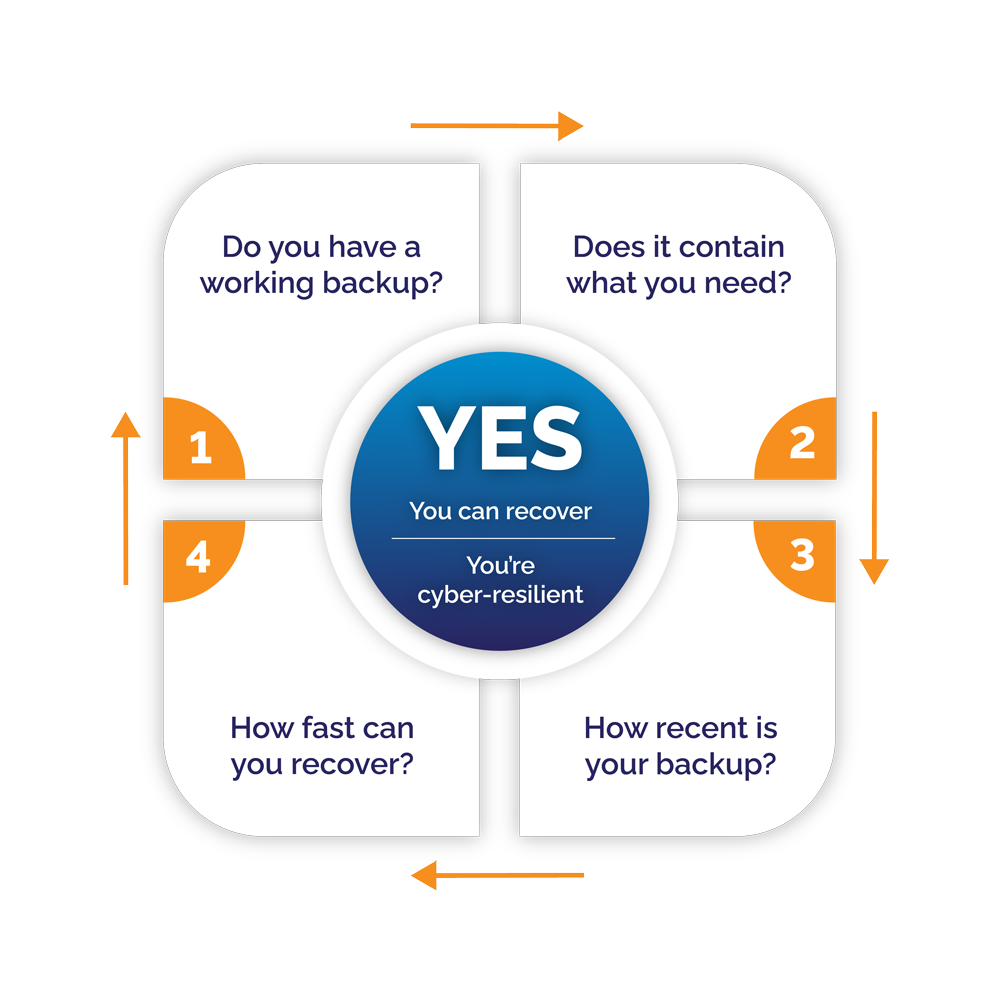
The four pillars of cyber-recovery
When designing your recovery strategy, there are 4 key pillars SMEs must account for. To make them actionable, we frame them as 4 questions you should ask when developing your recovery strategy. They are:
- Do you have working backups? This is always the place to start. Having a reliable backup and recovery strategy is critical to being cyber-resilient. In the event of a cyber-attack, you need to be able to restore your systems and data as quickly as possible.
- Does your backup contain all the data you need? Backups are only useful when they contain the data you need. This may sound obvious, but it’s easy to get wrong. For example, a common mistake is using file backups when you need an image backup (or vice versa). Make sure that you’re backing up everything you would need to fully restore business-critical operations in the event of a disaster.
- How recent are your backups? This is the classic RPO question. If your existing backups aren’t recent enough to be useful and meet your RPO objectives, you’re not as cyber-resilient.
- How fast can you recover? This is the RTO side of backup and recovery. In the event of a cyber-event, how soon can you restore normal operations? And I can’t overstate this point: make sure to test and confirm that your answer to this question is realistic.
How to be cyber-resilient in 2022
Now, let’s tie what we’ve covered so far together into some tactical steps. Given what we know, we can break what SMEs should do to ensure cyber-resilience into 3 key steps:
- Risk identification and mitigation planning
- Implementing the right backup system
- Having — and testing — a disaster response and recovery plan
Let’s take a closer look at each.
Risk identification and mitigation planning
Risk identification is all about quantifying your attack surface and exposure to threats. In 2022, for most SMEs, this means assessing the security posture of on-prem and cloud-based assets and making an informed decision on how to mitigate risk.
Here, SMEs can use network discovery tools and vulnerability scanners (e.g. Tenable Nessus, nmap, etc.) as well as policy audits to determine their current state, compare that to the risks facing their organization, and quantify mitigations. Here are a few common threats modern SMEs may identify in this process and ways to mitigate them:
| Threat | Mitigation |
|---|---|
| User clicks a malicious link | URL filtering |
| Ransomware infecting backups | Backup solutions that ensure backup integrity (e.g. CryptoSafeGuard) |
| Lateral movement of malware post-breach | Endpoint protection; micro-segmentation |
| Lack of insight to root cause of a breach | Forensics files included in backups (e.g. using Cyber Black Box) |
| Phishing | User training; intelligent spam filtering/firewalls |
The right backup system
Backups are the cornerstone of cyber-resilience and having the right system in place is a must. Of course, there’s no one-size-fits-all best backup solution for SMEs, but there are key questions you can ask to find the right solution for your organization.
- Does it allow you to create backups of all critical images and files?
- Does it support all 3 common types of backups?
- Does it support your cloud and on-prem platforms?
- Does it provide automation and scheduling that enables you to meet your RPOs?
- Does it provide mitigations against ransomware and malicious deletion?
- Does it enable recovery in the cloud or on-prem?
For more insights on selecting a specific backup solution, check out our “What’s the best backup software?” article.
Response plan and practice runs
With your risk profile quantified, mitigations in place, and backup plan rolling, the final step towards cyber-resilience is developing and testing your recovery strategy. Again, there isn’t a one-size-fits-all solution, but an effective response plan should have these characteristics:
- You can recover from a cyber-event in time equal to your RTO (or faster).
- You can recover critical systems anywhere; it isn’t tied to a single location or cloud provider.
- It accounts for common threats such as ransomware-infected backups and malicious deletion.
- You can selectively perform full or granular system recoveries as needed.
And, it’s imperative that you regularly and rigorously test your recovery processes! Make testing your recovery plan part of IT operations and consider the worst-case scenarios. A strategy for cyber-resilience that you’ve never tested is incomplete.
Final thoughts: Assess, iterate, and improve
Cyber-resilience isn’t an all-or-nothing thing, and what works today may not work next year (or even next week!). That’s why it’s imperative for SMEs to continuously test their cyber-resilience and recovery strategies, monitor the threat landscape, and iterate and improve over time.