TL;DR summary
Your data is your data. That’s one of the underlying principles of how we do business.
BackupAssist 365 provides the following features to help with careful data handling.
| Privacy |
|
| Sovereignty |
|
| Accessibility |
|
| Anonymity |
|
We’ll now elaborate on each of the aspects listed above.
(Note: if you are interested in the background context – why we take these approaches – then please refer to our companion article.)
Privacy
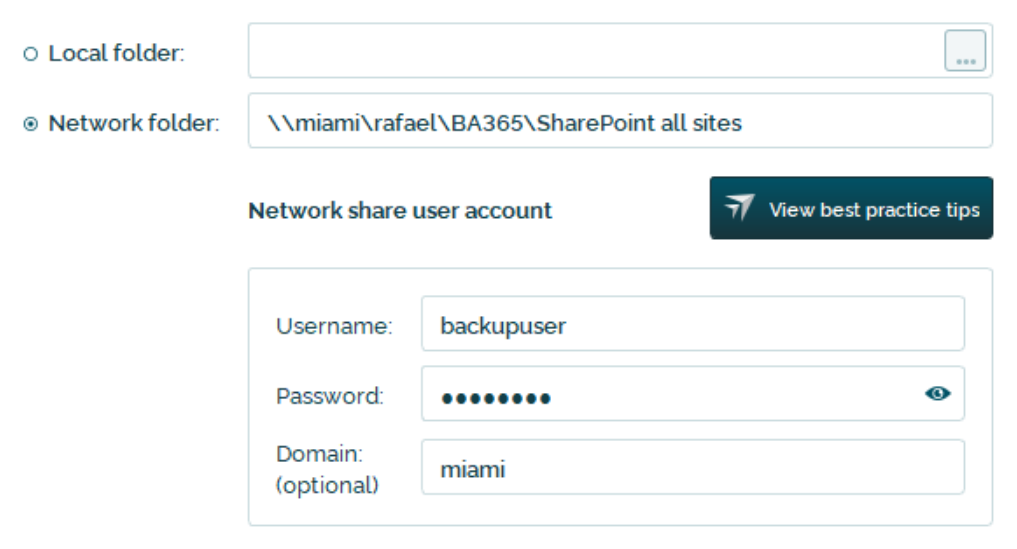
BackupAssist 365 has a “choose your own storage” approach, where you can decide where to store your backup data. You can choose a local disk, or network share.
Because you host your own data, it means that you control who has access to it.
BackupAssist has no way of accessing your data.
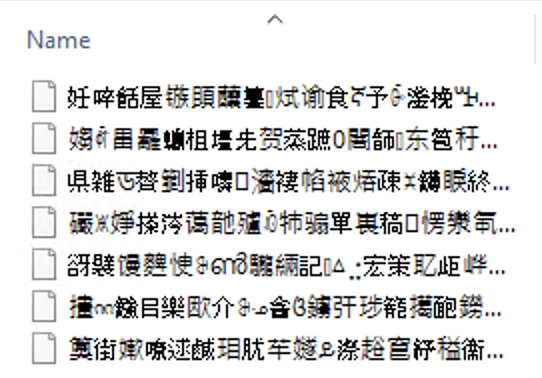
As a security measure, you may also choose to encrypt your file backups (SharePoint, OneDrive, Dropbox, Box, etc). Using the encryption feature means that a security breach of your underlying storage will not leak any data.
If you encrypt your file backups, an attacker will see only ciphertext:
(Note: encryption is not available for mailbox backups, only file backups.)
Sovereignty
As the logical flow-on from the “choose your own storage” approach, it means you can control the geographical location of the data.
Accessibility
A key consideration when choosing a backup solution is this: if you have a backup, how easy is it to access and restore the data?
BackupAssist was designed to address this issue.
Mailbox backups (Exchange, IMAP):
- You can take a copy of the PST file and open it in Outlook.
- Numerous 3rd party tools exist to open and extract information from PST files.
- You can use BackupAssist 365’s mailbox restore feature to upload the PST to a new mailbox.
File backups (SharePoint, OneDrive, Dropbox, Box, etc):
- Unencrypted backups can be restored directly by accessing the backup files.
- In Mirror mode, the files can be copied out directly.
- In Versioning mode, the filenames can be renamed to remove the version information suffix.
- All backups can be restored using BackupAsist 365’s file restore facility, and restored to a local directory or to a cloud storage location.
Anonymity
In the most stringent environments where this is required, a level of anonymity can be achieved if BackupAssist 365 is configured in the correct way.
Normally, there may be some small data leakage of email addresses via two channels:
- the BackupAssist 365 email reporting feature, and
- sending diagnostic information to our tech support helpdesk.
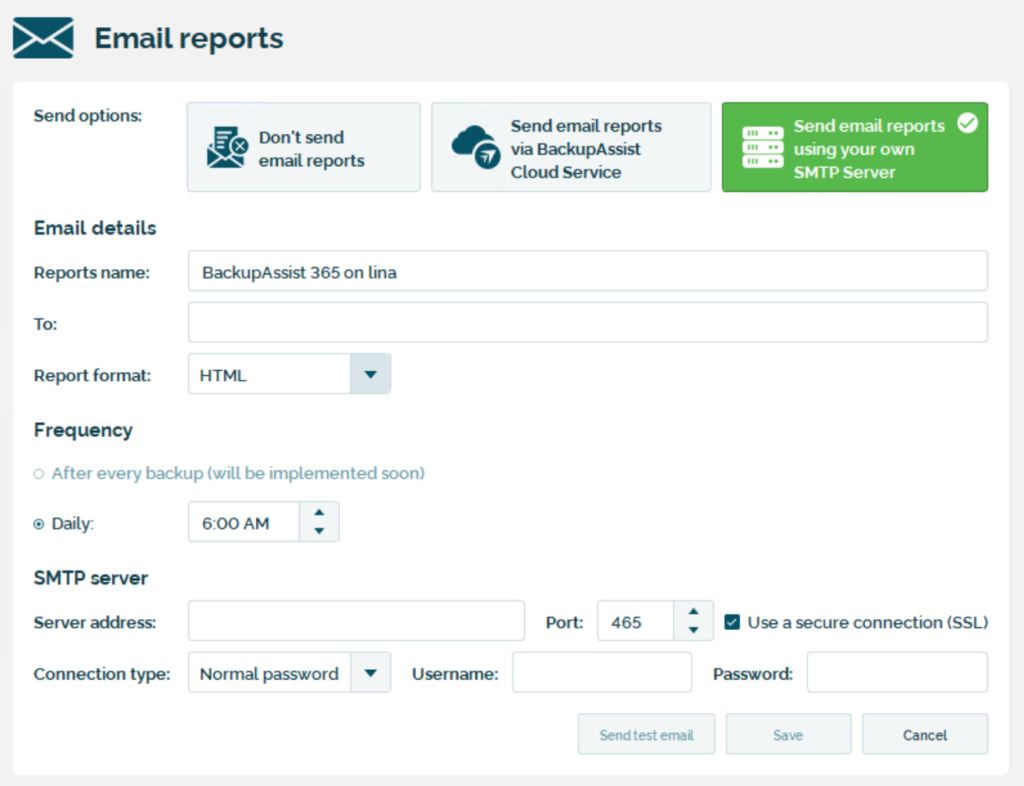
The leakage occurs because certain metadata (e.g. the list of email addresses for each mailbox that was backed up) gets sent to BackupAssist. For example, in the email report, email addresses are visible:
If this leakage needs to be avoided, then you can send email reports via your own SMTP server. This ensures that the email reports never pass through the BackupAssist servers.
Additionally, we recommend not sending diagnostic information to us.
Conclusion
BackupAssist 365 provides a high level of data privacy, sovereignty, accessibility and even anonymity. Your data is your data.
Do you have questions about this article? Contact our Client Success team and start a conversation.
Or better still – start your free 30-day trial of BackupAssist 365 today!