Spear Phishing has been on the rise lately, according to a number of recent posts by IT Professionals on Spiceworks. These kinds of targeted attacks can be extremely harmful to businesses if staff aren’t properly prepared, so in this article, we’re going to look at what Spear Phishing is, how your business can defend against it, and the role your server backup software will play in that defense.
Let’s dive in.
What is Phishing, and how is Spear Phishing different?

Let’s start by defining Phishing. Basically, it’s an attempt to trick people into divulging sensitive details (usernames, passwords, bank account info, credit card numbers, etc), or downloading a malicious software program, by masquerading as a trusted source. Most Phishing attacks often come in the form of emails (although social media is another source to be wary of), and they will often be fairly easy to spot. They’re usually sent in bulk by an attacker, to 1000’s of email addresses at a time in the hope that if you cast a broad enough net, you’ll catch a fish or two.
Phishing attacks will generally pretend to be from a large organization, and might include the organization’s logo and correct mailing addresses (as these are easy to acquire online). However, telltale signs of a Phishing attack will often be the use of poor grammar and/or spelling errors, links to non-official web URLs (although often these will attempt to look legitimate by changing just one letter in the real URL), and broad or generalized messaging in the content of the email. For example:
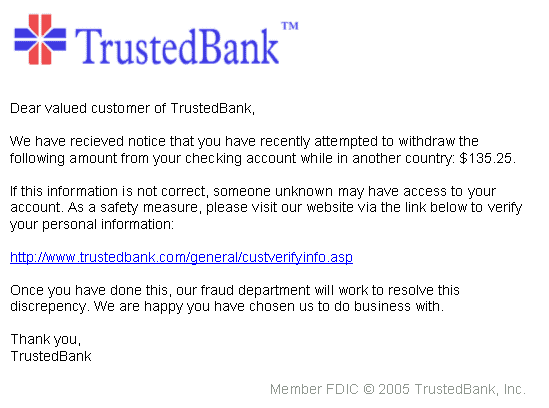
Fortunately, email providers and spam filters are getting better and better at recognizing and blocking these kinds of generic Phishing emails. And as we mentioned, those that do slip through are often quite easily recognized as suspicious, even by untrained staff.
Where things get more dangerous, is Spear Phishing.
Spear Phishing is a very targeted form of Phishing attack, where attackers will target a specific company and even specific people within that company, rather than sending out bulk emails to every email address they can get their hands on. This kind of attack is much more sinister, because the attacker will often tailor the email to the recipient. Spear Phishing usually involves some form of social engineering on the part of the attacker, and will often appear to come from somebody high-ranking within the organization.
In the Spiceworks topic we mentioned earlier, the email appeared to come from the CEO of the target company – using first and last name with a Gmail address.
For obvious reasons, these kinds of attacks are much more difficult for non-educated staff to detect, and have a greater chance of being successful.
So how can I prevent these attacks?

Preventing Spear Phishing comes down to educating employees above anything else. Social engineering attacks like Spear Phishing are designed to be convincing, and as such they can be difficult for uneducated coworkers to notice until it’s too late. But they will almost certainly never be perfect, and if your employees/colleagues are aware of the potential for these attacks, your business should be able to prevent the vast majority of attackers from getting what they want.
The best and most effective step you can take towards thwarting potential Spear Phishing attacks is to simply make staff aware of them. Show them examples of what Spear Phishing looks like, and caution them to be on the lookout for anything that seems even remotely out of the ordinary when it comes to email requests – even from seemingly legitimate sources.
There are even a number of 3rd party companies who offer training programs in recognizing these kinds of attacks, and can perform ‘drills’ where they send dummy Spear Phishing emails to your staff and track open and click rates to raise awareness in your business.
Another technique can be to implement policies and procedures, wherein sensitive information or financial transactions cannot be disclosed or actioned except through specific channels, which have safeguards in place against attacks of this kind. Of course, the type of business you run and any other number of variables will determine how viable this option is for you.
Finally, you’ll want to make sure you have software in place that can reduce the damage these kinds of attacks can cause. This can include email filtering that can catch the emails before they hit staff’s inboxes, or anti-virus software that can stop malicious software from being installed if a coworker hits a malicious link. And of course, your final line of defense is always going to be your backup solution!
A watertight backup strategy is what ensures that even if everything else fails, you can always recover safely.
They’ve got me. What do I do now?

Well, once you’ve been hit by a successful Spear Phishing attack, how you can best respond will depend on what the attackers were trying to achieve. If they were after money directly, via a transfer or access to bank accounts for example, then once they’ve stolen what they came for unfortunately the matter is probably out of your hands. Your bank and/or the police are quite likely the only avenue here, other than recovering the system and changing log-in details to make sure the attacker cannot get back in. Plus, as we mentioned above, you can make sure all staff are fully trained and educated on how to recognize and handle Spear Phishing attacks, to greatly reduce the likelihood of future incidents occurring.
If, on the other hand, the aim of the attack was to install ransomware or some other form of malware onto your system, then provided you have good backups, cleaning up and reducing the potential for any serious damage is a much more straightforward process.
In essence? Nuke the system from orbit and recover to bare-metal from a backup run before the attack took place.
Much as with any ransomware and most forms of malware attacks, secure backups are your absolute best line of defense from serious damage. It’s what ensures that you can always recover to a point before the attack took place, and with minimal data compromised or lost.
It’s just another reason why having reliable, recoverable backups is so important for all businesses of all shapes and sizes.
Want to hear more about real world examples of Spear Phishing attacks? Check out these Spiceworks topics where IT Pros have described their experiences:
Topic: Very Targeted Phishing Attack
Topic: Targeted Phishing Attack
Topic: Phishing Technique with Similar Domain Name
Topic: Phishing Attempt 38k Wire Transfer Almost Went Through
Topic: Concerns about Phishing Email
Has your company been the target of Spear Phishing? Did backups save your bacon?
Leave your story in the comments below, tweet it to us @BackupAssist or post it to Facebook.
Share this article to raise awareness and make life harder for attackers.
1 thought on “Spear phishing is on the rise – know how to spot it!”